NoSQLi Lab
With the rise in popularity of NoSQL I figured it was time to build a lab so I could have a play with the different techniques used to attack them. This was the result...
Seeing as I've already played with Redis for some development work I decided to go with MongoDB here. I have built two different scenarios in this lab, an equivalent of the SQLi " or 1=1" vulnerability and also a new type of attack, which is specific to NoSQL, script injection. I might add more later but these were good for a start.
The lab is easy to install, the only problem is making sure your Linux distro includes the latest MongoDB drivers for PHP, this is the right one:
php-mongodb - MongoDB driver for PHPAnd this is the wrong one:
php5-mongo - MongoDB database driverThe lab is available on Github at https://github.com/digininja/nosqlilab. The following shows how to get it working on Debian Stretch. Last time I checked, Jessie uses the older version of the drivers and so wouldn't work.
apt-get update && apt-get dist-upgrade
apt-get install php-mongodb apache2 vim mongodb git php
cd /var/www/html/
rm index.html
git clone https://github.com/digininja/nosqlilabIf you then browse to your IP you will hopefully get the lab home page:
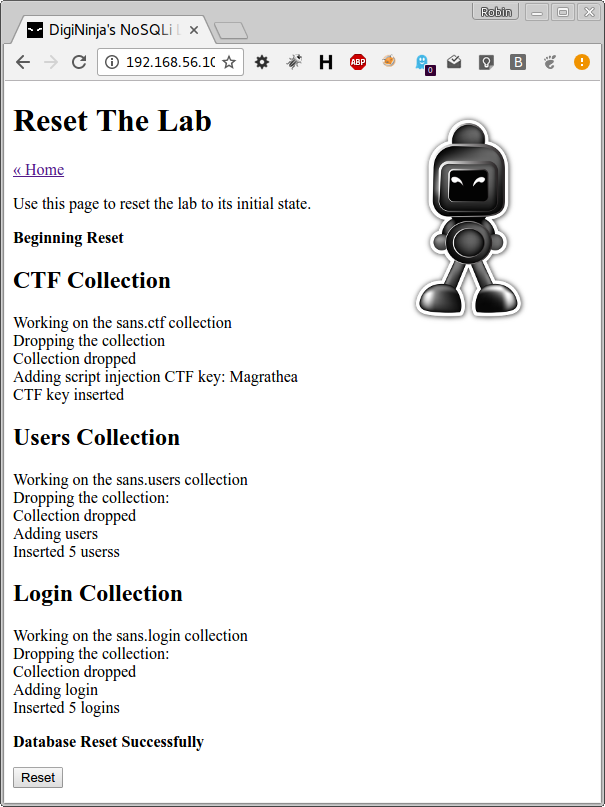
The first thing to do is to populate the database with the test content, this is done with the "Reset Database" link. If this works you should not see any errors and the page should end with the message "Database Reset Successfully":
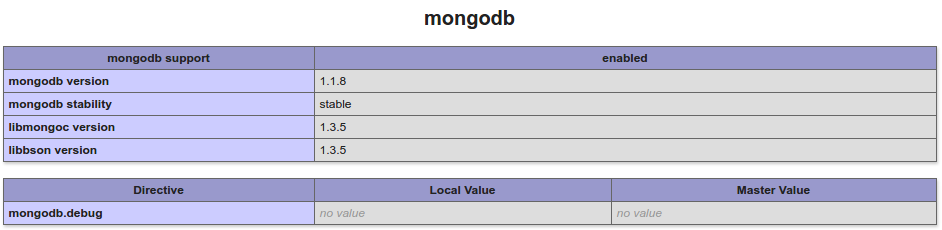
If you get a page full of PHP then you have either missed installing PHP or for some reason it is not enabled, start your debugging looking there. If the page starts to render but does not finish and you do not get the success message then it may be that you have not got the MongoDB libraries, check the Apache error log. You can also check by looking at the phpinfo() page, it should look something like this:
Once everything is working there are two vulnerable pages, "Guess The Key" and "User Lookup". I'm not going to go through how to attack them as there are plenty of tutorials on NoSQLi out there. A good place to start is the OWASP Testing for NoSQL injection guide. If you get really stuck, I've provided some sample solutions hidden away in the solutions section.
Any problems with any of it, raise an issue in Github and I'll take a look at it. I'm not a NoSQL expert and most of this has been built by trial and error so if you spot problems, or feel you can improve things, feel free to submit pull requests.

