Burp Intruder Attack Types
Wed 9th Nov 11
I use Burp Intruder quite lot when doing web app tests but for some reason I always have to stop and think which attack mode I need when going after multiple parameters so figured if I write it down then it may help me remember what is what and help other people who aren't sure.
To show the different modes I'll use this very simple form:
<form method="post" action="/burp_test.php">
Username: <input name="username" value="" type="text" /><br />
Password: <input name="password" value="" type="password" /><br />
<input type="submit" value="login" />
</form>And I'll use two word lists, users:
- fred
- joe
- george
- guest
and passwords:
- password
- admin
- guest
- god
- letmein
Even though here I am talking about just two parameters it should be easy for people to extrapolate these examples out to more.
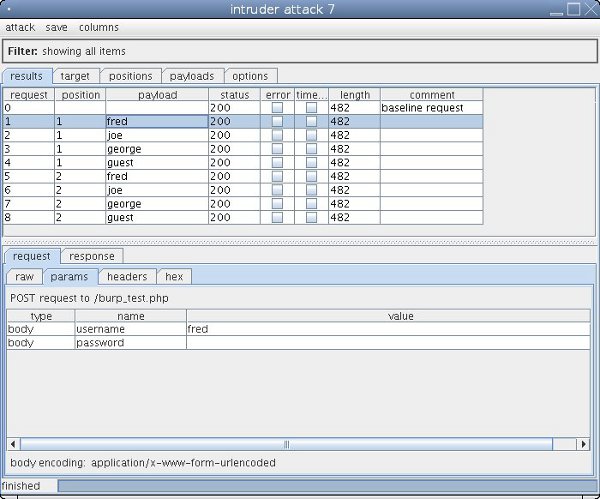
Sniper
Sniper mode takes a single input list and uses it against each parameter in turn, leaving the rest of the parameters as their default value. For my four word user list it will make eight requests, four against the username field and four against the password field.
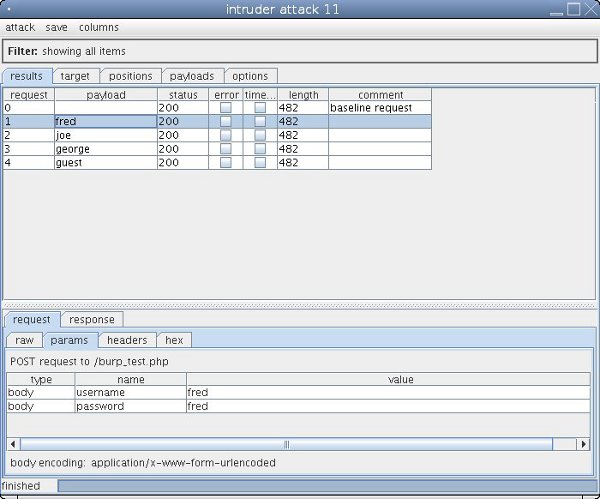
Battering Ram
Battering Ram also takes a single list but it uses each word against every parameter in a single request so this time there will only be four requests for my four usernames.
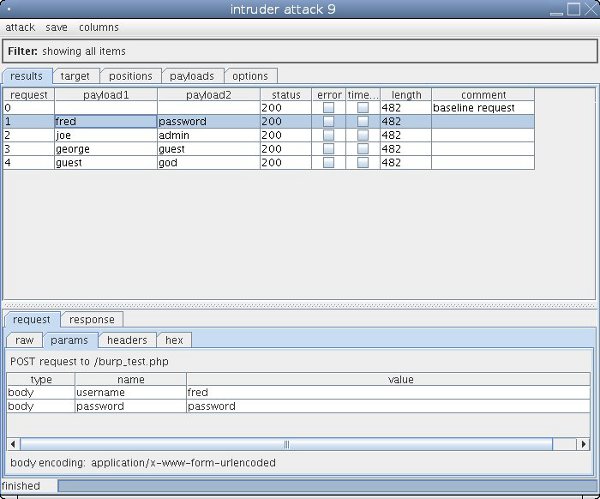
Pitchfork
Pitchfork is similar to Battering Ram but this time taking a list of words per parameter. If the lists do not match in length then the requests will stop when the shorter list runs out. In this example it will make four requests.
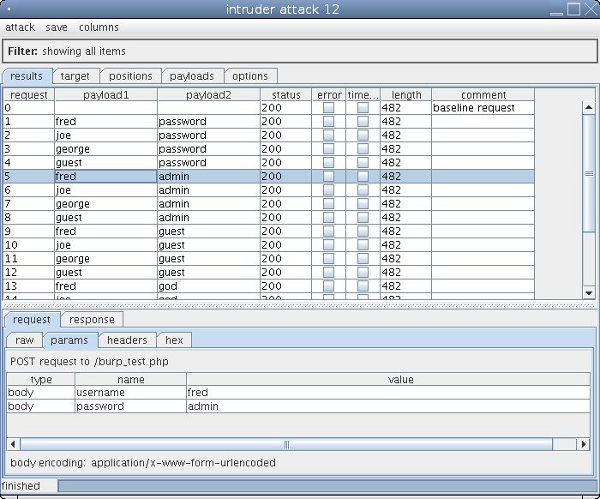
Cluster Bomb
Finally Cluster Bomb mode, this is the one you would expect to use in this scenario. It takes two lists and runs every word in the first list against every word in the second, i.e. your standard password brute force attack. Four usernames with five passwords makes a total of 20 requests.