Hacking NASL Scripts
Thurs 24th Mar 2016
During a recent test I saw the Nessus plugin "Microsoft Windows SMB Registry : Autologon Enabled" for the first time. This plugin reads the auto login credentials from the registry and reports on them [1]. This was a great find at the start of the test, the only problem is that Nessus has a policy of obfuscating any passwords that it finds which aren't default so the report came out like this:
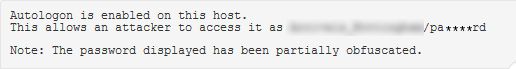
I tried various methods of recovering the credentials manually but for some reason each try failed so I figured why not go back to Nessus and hack the NASL script and remove the obfuscation.
As far as I know, there is no way to get the NASL filename from inside Nessus so you have to find the appropriate file by searching for it in the plugins directory, on Linux, usually /opt/nessus/lib/nessus/plugins. The best thing to search for is the plugin id, in this case 10412, as it is registered by the script using the script_id function:
$ grep "script_id(10412)" *
smb_reg_autologon.nasl: script_id(10412);As a side note, a problem I've had in the past is that bash globbing [2] wasn't happy with the number of files in the plugins directory so if you get errors trying to search like this you can do this as an alternative:
$ find . -type f -exec grep -H "script_id(10412)" '{}' \;This found the file smb_reg_autologon.nasl which I could have probably guessed just by looking at file names but finding it like this just works.
My initial assumption was I could just edit the file, the change is quite simple:
--- smb_reg_autologon.nasl 2016-03-10 23:25:09.250376471 +0000
+++ /tmp/smb_reg_autologon.nasl 2016-03-18 20:57:40.059226761 +0000
@@ -82,7 +82,7 @@
+ crap(data:"*", 6)
+ substr(password[1], (strlen(password[1])-1));
rep = 'Autologon is enabled on this host.\n' +
- "This allows an attacker to access it as " + username[1] + "/" + cleaned +
+ "This allows an attacker to access it as " + username[1] + "/" + password[1] +
'\n\nNote: The password displayed has been partially obfuscated.';
security_hole(port:port, extra:rep);I did this and reran the scan but still got the same, obfuscated result. Next thing I tried was restarting Nessus, this didn't work either.
After talking to some friends it turns out Nessus compiles the plugins to byte code before using them [3]. To get it to do this for my modified script I've been told I need to disable signature checking by setting by editing the nessusd config file. All the docs I can find about doing it say to edit /opt/nessus/etc/nessus/nessusd.conf but I've not got that on my machine, I've got /opt/nessus/etc/nessus/nessusd.conf.imported instead so I edited that. The setting you need to change is this one:
# Should consider all the NASL scripts as being signed ? (unsafe if set to 'yes')
nasl_no_signature_check = noObviously, set it to yes.
And then recompile the scripts with:
nessusd -rAfter this I reran the scan and got my credentials:
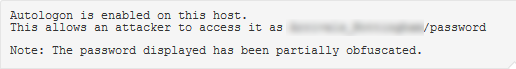
As you can see, the changes are pretty simple and got me the credentials without wasting time trying to find out why I couldn't manually extract the creds from the registry. This process will work for any of the scripts which obfuscate passwords or any other data, all you need to do is find the script, make the changes and then recompile.
[1] For more information see this TechNet article https://technet.microsoft.com/en-gb/library/cc939702.aspx. (Continue)
[2] Before people mail me to tell me how much better globbing is in their shell, I don't care, I use bash and have no intention of switching. And Vim rocks! (Continue)
[3] This is why you some times get a really slow progress bar when starting Nessus after an update, it is compiling all the new scripts it just got. (Continue)

