Windows RDP client, show login page
Wed 24th Nov 16
Occasionally while doing external infrastructure tests I'll find an exposed RDP server, when I do, I like to connect and look at the desktop login prompt as it can reveal some interesting information about the server or the company it belongs to. If you try to connect using the standard Windows RDP client, the client asks for the login credentials and so hides the desktop from you. There is a way around this but as I do it so infrequently I usually forget what it is so I'm publishing it here for the next time I need it. Thanks to Andrew and a few others on Twitter for reminding me this time.
This is the process:
- Open the RDP client as usual
-
Fill in the host name and then select "Show Options" to reveal the "Save As..." button, use this to save the details:
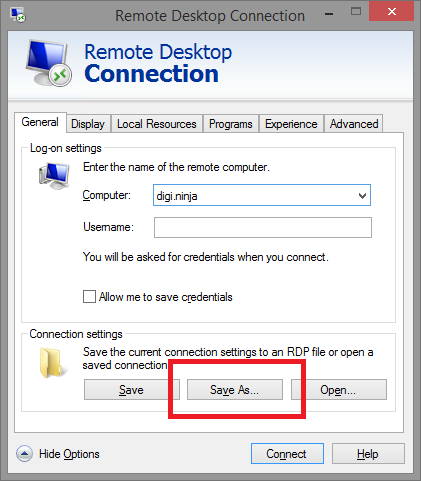
- Open the saved file in a text editor and add the following line:
enablecredsspsupport:i:0 - Save the file and then open it by either double clicking or using the "Open" button in the RDP client
Now when you connect you should go straight through to the Windows login page rather than being asked for credentials by the client.
If this does not work for you then it may be that the server has Network Level Authentication (NLA), enabled. This is an additional layer of authentication which is done before the RDP session is established and helps restrict access to RDP sessions.
If you are curious what can be revealed, take a look at this login page I found through a Google image search:
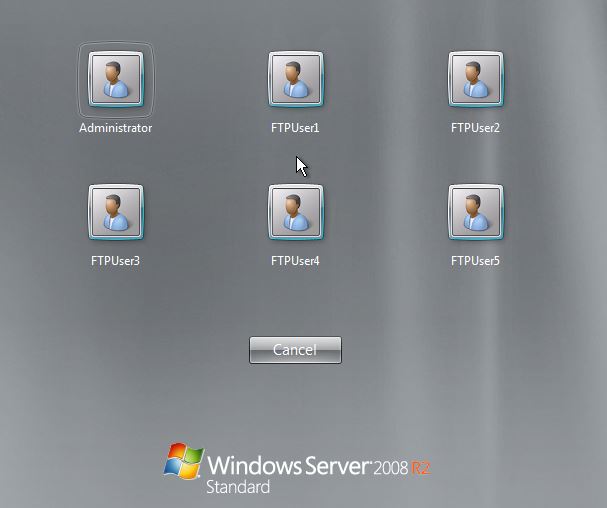
This shows six users who are prime for brute force login attacks. The page can also reveal domain names if the users shown are domain users and, occasionally, I've seen overlays which show information about the server such as internal IP addresses, disk space, hostname/domain and other mildly sensitive information.
If your server shows this information, the site where the screenshot above comes, VSYSAD, from contains information on how to disable it. I've not tried this but it seems to make sense.

